The secret rulebook behind every tap-and-go payment (Part 4)
How everyday roles and famous breaches turn PCI DSS from theory into daily discipline
Chapter 4: ROLE-BASED AWARENESS
When people first learn about PCI DSS, it can feel abstract, twelve requirements, dozens of controls, hundreds of acronyms.
But compliance doesn’t happen in the document library; it happens in the choices people make each day.
Every commit, every deployment, every configuration file either strengthens or weakens the protection of cardholder data.
This chapter takes you inside four everyday roles, Solution Architect, Software Developer, Tester, and Project Manager to show how each one keeps the organisation within the PCI guardrails.
You’ll see that PCI isn’t the job of “the security team.” It’s a shared language of safety.
4.1 The Solution Architect, Guardian of Boundaries
The architect’s super-power is design foresight. Long before a single line of code is written, you decide where card data will flow and where it won’t.
That boundary, more than any single control, determines the size of your PCI scope and the effort to keep it secure.
Defining the CDE
Start every payment-related project by drawing the data-flow diagram.
Ask, step by step:
Where does card data enter?
Where is it transformed, stored, or transmitted?
Who or what touches it on the way out?
Every arrow on that diagram is a potential exposure.
Architects who design without mapping data flow are like electricians wiring a house blindfolded.
Example:
An architect at an e-commerce firm noticed that a marketing plug-in was receiving full card numbers via analytics tags. By simply changing the integration point to fire after tokenisation, he removed an entire vendor from scope, saving the company tens of thousands in audit costs.
Building Segmentation and Isolation
Think of segmentation as the moat around your castle.
Your PCI zone should be a small, self-contained island: isolated networks, restricted subnets, minimal connectivity to non-PCI systems.
Use:
Separate VPCs or network segments for the CDE.
Firewall rules allowing only required traffic.
Jump hosts or bastions for administrative access.
Golden rule: If a server doesn’t need to talk to the CDE, it must not be able to.
Designing for Tokenisation and Outsourcing
Every architect faces a pivotal choice: build or delegate?
If a third-party payment gateway can safely process card data, let them.
By externalising the sensitive part, you reduce your internal exposure and shift the compliance burden to a specialist whose entire business is PCI.
However, you must validate the vendor’s Attestation of Compliance (AoC) and ensure contracts specify PCI responsibilities.
Outsourcing does not mean abdication, it means partnership under written assurance.
Architect’s Checklist
Card data flow mapped and documented
Network segmentation diagram approved
Encryption and tokenisation designed end-to-end
Vendor AoCs reviewed and stored
Non-functional requirements include PCI controls (IAM, monitoring, DR)
Reflection Pause
If you drew your current system’s boundaries today, could you clearly mark which components are in PCI scope?
If you can’t, that’s your first priority tomorrow.
4.2 The Software Developer, Defender of Data
Developers are closest to the raw material of compliance: code.
A single logging statement can undo a million dollars of architecture.
Yet, developers are also best placed to stop problems early because they control how data is handled at the source.
The Rule of Least Exposure
The simplest way to stay compliant is never handle real card data.
Where possible, use client-side tokenisation or hosted payment pages so the browser sends the PAN directly to the payment provider, not to your API.
Your backend receives a harmless token instead of the real number.
If you must handle CHD, immediately encrypt or tokenise it before any persistence or logging occurs.
Secure Coding Habits
Validate inputs strictly. Never trust user data, sanitise, whitelist, and type-check.
Use parameterised queries. Prevent SQL injection.
Mask logs. Replace sensitive digits with
XXXXor omit them entirely.Protect secrets. Store keys in managed services (AWS Secrets Manager, Azure Key Vault).
Avoid real data in tests. Use gateway-supplied dummy cards.
Story: The Danger of Debug Logs
During integration testing, a developer left console.log(request.body) active inside a Lambda. It worked fine until real payments began. Overnight, hundreds of PANs appeared in CloudWatch logs.
No breach occurred, but the company’s entire observability stack became in-scope for PCI. It took weeks to cleanse and re-architect.
The fix? Introduce a logging filter middleware that automatically masks any field named card, pan, or cvv before writing logs.
A ten-line utility now protects millions of transactions.
Code Review and Automation
Security reviews shouldn’t depend on human memory. Integrate Static Application Security Testing (SAST) and Dependency Scanning into CI/CD pipelines.
Flag issues early, before merge.
Treat a failed security scan the same way you treat a failed unit test.
Developer’s Checklist
No CHD/SAD logged or stored
Encryption libraries validated and tested
Secrets managed through approved vaults
Automated scanning in pipeline
Dummy cards only in non-production
Reflection Pause
Open your latest codebase. Search for the words “card”, “cvv”, “pan”, or “payment”.
Would any of those lines raise a red flag to an auditor?
If yes, fix them today, future-you will thank present-you.
4.3 The Tester, Detective of Exposure
Testers are the quality guardians.
While developers ensure data is handled correctly, testers confirm that nothing slips through the cracks.
They are the ones who can catch data leakage before it becomes a breach.
Testing for Data Safety
When testing payment flows:
Inspect responses and logs. Ensure no API returns or stores full PANs or CVVs.
Check error handling. Failed transactions must never echo card details.
Verify TLS. Capture network traffic and confirm encryption throughout the chain.
Validate data masking. Reports, dashboards, and exports should display only partial PANs (e.g.
**** **** **** 1234).
Negative Testing and Abuse Cases
Attackers don’t follow the happy path, and neither should you.
Try:
Submitting malformed payloads or very long numbers.
Attempting to upload files where text is expected.
Replaying valid tokens twice.
Your goal isn’t to break the system maliciously, but to prove that defences hold even under stress.
Story: The QA Hero
At a Sydney start-up, a tester noticed that refund emails included full card numbers, a feature added “for convenience.”
She raised a ticket, and it turned out the template engine was using raw API responses.
Had those emails been sent to customers, thousands of PANs would have left the CDE.
Her curiosity saved the company from a breach and a fine.
That’s the value of critical testing.
Automating PCI Validation
Use scripts or static analysis tools that search for PAN-like patterns (\b[0-9]{13,19}\b) in logs and databases.
Run them nightly. If they ever match, alert immediately.
Many organisations integrate these scans into CI/CD or SIEM systems. Prevention through automation keeps humans from missing patterns.
Tester’s Checklist
No card data in responses or logs
TLS validated end-to-end
Reports show masked data only
Abuse and replay scenarios tested
Automated pattern scans in place
Reflection Pause
When was the last time your QA suite explicitly checked for data masking or encryption?
Testing functional correctness is good; testing data hygiene is better.
4.4 The Project Manager, Coordinator of Compliance
Project Managers may not configure firewalls or write code, but they decide whether PCI tasks are prioritised or postponed.
Their influence determines if compliance stays visible or quietly drifts into “later.”
Making Compliance Part of Delivery
In agile terms, PCI is not a “nice-to-have.” It’s a definition-of-done.
Every user story that touches payments should include acceptance criteria such as:
“All card data tokenised before storage.”
“Logs verified for masking.”
“Security review approved.”
By embedding compliance into the backlog, PMs prevent last-minute scrambles before audits.
Tracking Evidence and Attestations
PCI audits thrive on documentation.
PMs ensure:
Vendor AoCs are collected and renewed annually.
Architecture diagrams and DFDs are version-controlled.
Training records are stored.
Jira or Confluence pages capture proof of each requirement.
A well-maintained evidence trail turns audit season from panic to paperwork.
Scheduling Security and Training
Requirement 12 mandates regular awareness training.
PMs coordinate these sessions, ensuring new joiners complete induction within 30 days and all staff refresh annually.
They also schedule quarterly vulnerability scans and annual penetration tests in the roadmap so they’re never forgotten when delivery pressure mounts.
Story: The Project That Forgot Security
A mobile wallet project once treated PCI items as “phase 2.” The launch went ahead with tokenisation incomplete. Within weeks, a partner bank refused integration until the system passed PCI validation. The resulting delay cost more than the original sprint budget.
The PM later said, “We learned the hard way that compliance work is delivery work.”
PM’s Checklist
PCI requirements built into backlog
AoCs collected and tracked
Security scans and pen-tests scheduled
Training compliance reported monthly
Risk register includes PCI items
Reflection Pause
Open your project board.
Are PCI-related stories visible, with owners and due dates?
If not, they’ll quietly slip behind feature requests and reappear only when auditors call.
4.5 The Shared Responsibility Mindset
PCI DSS works only when everyone pulls together.
Architects limit exposure; developers code securely; testers verify integrity; PMs keep the machine disciplined.
It’s like an orchestra, different instruments, one melody: protect cardholder data.
Cross-Role Collaboration
Design reviews: Architects and developers discuss data flows with testers present, so everyone agrees on boundaries before a single deployment.
Security stand-ups: Once a fortnight, each squad surfaces new risks or near-misses.
Incident simulations: PMs run tabletop exercises, “What if logs leaked CHD?”, so roles are clear when reality strikes.
These rituals turn PCI from a static document into a living culture.
4.6 Mini-Review Quiz
What is the architect’s primary goal during PCI design?
Why should developers avoid handling real card data whenever possible?
Name two ways testers can confirm that card data isn’t leaking.
What evidence must project managers collect to support audits?
How does embedding compliance tasks in sprints improve outcomes?
4.7 Summary, The Everyday Champions
PCI compliance is not a project milestone; it’s a habit.
Architects draw boundaries, developers guard data, testers catch leaks, and PMs keep the rhythm.
When each role treats security as part of craftsmanship, PCI DSS stops feeling like bureaucracy and starts feeling like pride in doing things properly.
“A compliant system is simply a secure system that was built by people who cared.”
Chapter 5: Real-World Mistakes and Lessons
When you read a PCI DSS control, “encrypt transmission” or “restrict access”, it can sound abstract, even bureaucratic. But behind every clause sits a painful story: a company that learned the hard way what happens when controls fail.
These are not cautionary tales from unknown startups; they’re from global enterprises with entire departments dedicated to security. The mistakes were small, the consequences enormous.
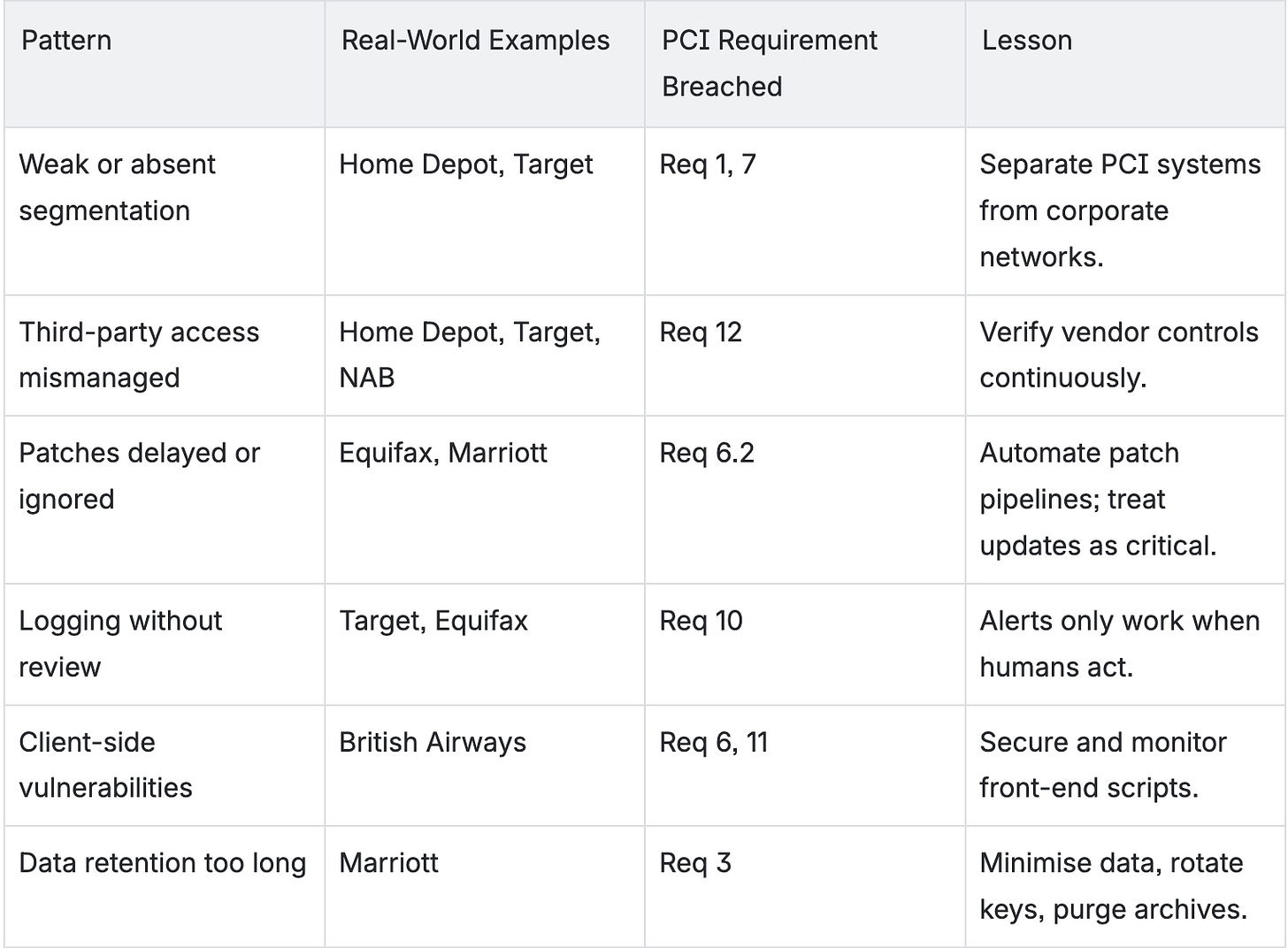
5.1 The Home Depot Breach; The Chain-of-Trust Failure
In 2014, Home Depot, one of the world’s largest home-improvement retailers, suffered a data breach that exposed 56 million customer payment cards.
What Happened
Attackers didn’t storm the main network head-on.
They entered through the credentials of a third-party vendor, a small heating and air-conditioning contractor who had remote VPN access for billing. Once inside, the attackers moved laterally into Home Depot’s point-of-sale (POS) environment and installed malware that captured card data in memory as transactions were processed.
PCI DSS Violations
Requirement 7 & 8: Access not restricted by business need-to-know; shared credentials between vendor systems.
Requirement 11: Lack of intrusion detection and log correlation.
Requirement 1: Weak network segmentation, once the attackers entered, they could move freely.
The Root Cause
The weakest link wasn’t technology, it was trust without verification. The vendor connection bypassed strong access controls, and network segmentation between corporate and POS systems was incomplete.
The Cost
Home Depot paid over US $179 million in settlements and fines, not including brand damage and years of litigation.
The Lesson
For architects: segmentation is sacred. Vendors should connect through tightly scoped APIs or bastion gateways, never directly into sensitive networks.
For project managers: always collect and verify vendor AoCs and monitor their access continuously.
For everyone: your PCI scope includes your partners, whether you like it or not.
5.2 Target; When Monitoring Exists but Nobody Looks
In 2013, Target Corporation experienced one of the most publicised PCI-related breaches in history. Around 40 million cards were compromised, plus 70 million customer records.
What Happened
Just like Home Depot, the attackers came in through a third-party vendor, in this case, an HVAC maintenance company. They used stolen credentials to access Target’s internal network and deploy malware on POS terminals.
The tragedy?
Target’s intrusion detection system (FireEye) actually raised alerts in real time. But those alerts were ignored. The SOC team was overloaded and under-trained.
PCI DSS Violations
Requirement 10: Logs and alerts must be actively reviewed.
Requirement 12: Lack of trained personnel and effective incident-response process.
Requirement 5: Failure to keep endpoint protection signatures updated.
The Cost
More than US $290 million in settlements, legal fees, and remediation plus a CEO resignation and multi-year reputation hit.
The Lesson
Monitoring is meaningless without human vigilance.
PCI doesn’t just ask for logs; it asks for log review.
Architects and PMs must ensure that monitoring alerts flow to trained teams who have authority to act. Testers can help by simulating incidents and confirming alerts trigger correctly.
“Detection without response is decoration.”
5.3 British Airways; The JavaScript Injection Disaster
In 2018, British Airways was fined £20 million (AUD ≈ 40 million) after a cyber-attack redirected customers to a fraudulent payment page.
What Happened
Hackers injected malicious JavaScript into British Airways’ website. When customers entered payment details, the script silently sent card data to an attacker-controlled domain.
The compromise lasted two months and affected about 400,000 cardholders.
PCI DSS Violations
Requirement 6: Failure to maintain secure web applications and patch vulnerabilities.
Requirement 11: Insufficient change-detection mechanisms on scripts.
Requirement 10: Lack of logging around client-side integrity changes.
Root Cause
The attackers exploited outdated third-party libraries and unmonitored front-end changes, a blind spot in most PCI programs that focus on back-end servers.
The Lesson
For developers: PCI applies to client-side code too.
If your JavaScript collects payment data, treat it like part of the CDE. Use sub-resource integrity (SRI) checks, content-security policies (CSPs), and code signing to prevent tampering.
For architects: maintain an inventory of external scripts and libraries. Implement automated integrity checks in CI/CD.
Even the front-end is a door; lock it.
5.4 Marriott International; When Data Lives Too Long
In 2018, Marriott International revealed that attackers had accessed the guest reservation system of Starwood, a hotel chain it had acquired. The intrusion had persisted undetected for four years, exposing data from over 383 million guests, including card numbers, passport details, and addresses.
What Happened
Attackers breached Starwood’s network in 2014, well before the merger. The compromised systems including databases containing encrypted card data, were migrated into Marriott’s infrastructure without thorough re-assessment. The attackers retained access post-migration.
PCI DSS Violations
Requirement 6 & 11: Inadequate vulnerability testing and failure to re-validate security after major changes.
Requirement 3: Long-term storage of cardholder data without re-encryption or key rotation.
Requirement 10: Insufficient monitoring and anomaly detection.
The Cost
Marriott was fined £18.4 million by the UK Information Commissioner’s Office and spent hundreds of millions on remediation and customer support.
The Lesson
Architects: every acquisition or major system migration resets your PCI clock.
Always perform a fresh CDE scoping and validation exercise.
Never assume the inherited environment is compliant, compliance is not transferable.
Project Managers: treat mergers, cloud migrations, and platform rebuilds as PCI-impacting events requiring new risk assessments.
5.5 Equifax; Patch Management and the Cost of Delay
In 2017, Equifax, one of the largest credit-reporting agencies, suffered a breach that exposed personal and financial data of 147 million people worldwide. Although not strictly a PCI merchant, the event demonstrates a perfect storm of PCI DSS violations.
What Happened
A known vulnerability in Apache Struts (CVE-2017-5638) had been publicly disclosed in March 2017. Equifax failed to patch it for months. Attackers exploited the flaw, accessed databases containing card and identity data, and exfiltrated it undetected.
PCI DSS Relevance
Requirement 6.2: Install critical patches within one month of release.
Requirement 11: Regularly scan and test for new vulnerabilities.
Requirement 10: Ensure logging is centralised and alerts are reviewed.
The Cost
Equifax paid over US $1.4 billion in fines, compensation, and upgrades and permanently damaged its brand credibility.
The Lesson
For developers and PMs: treat vulnerability notifications like fire alarms, not calendar reminders.
For architects: build automatic patch pipelines; don’t rely on human tracking.
For testers: verify patch levels in environments as part of regression testing.
A single missed update can undo every encryption key and firewall you’ve deployed.
5.6 NAB (National Australia Bank); The Cloud Misconfiguration Wake-Up Call
In 2019, National Australia Bank (NAB) publicly disclosed that the personal details of about 13,000 customers had been accidentally shared with a third-party data-validation service.
What Happened
During a routine system migration, customer information including names, addresses, and account numbers, was uploaded to a cloud server operated by an external provider without proper redaction or encryption.
Although the exposure was accidental and quickly contained, it prompted intense regulatory scrutiny because NAB is a card issuer and PCI DSS Level 1 entity.
PCI DSS Implications
Requirement 3: Data not adequately protected before transmission.
Requirement 7: Data shared beyond business need.
Requirement 12: Lack of defined data-handling process for external validation.
The Lesson
Even in highly mature institutions, configuration drift and human error are constant risks.
For architects: implement data-loss prevention (DLP) tooling and enforce encryption at upload.
For PMs: every data exchange with a third-party vendor must pass a PCI data-handling checklist before execution.
“It wasn’t a hack, it was a handshake done carelessly.”
5.7 Lessons Across the Board
After studying these incidents, several recurring themes emerge.
Each one maps directly to PCI principles but, more importantly, to human behaviour.
The moral is clear: non-compliance rarely comes from malice.
It comes from small oversights, an unpatched system, a forgotten script, a blind trust in a partner.
5.8 Reflection Pause
Take a quiet moment and consider your own environment.
Do you know every third-party system that can reach your CDE?
Who reviews alerts when your monitoring tool screams in the middle of the night?
How long is payment data retained in your databases or backups?
Are there front-end scripts on your payment pages that no one “owns”?
Write down three small actions you can take this week to reduce your organisation’s PCI risk.
They might feel trivial but so did those missed patches, unreviewed alerts, and forgotten test logs that triggered global headlines.
5.9 Mini-Review Quiz
Which PCI requirements did the Home Depot breach violate, and how?
What was the fundamental failure in Target’s monitoring process?
Why does client-side JavaScript fall under PCI scope, as shown by the British Airways incident?
What compliance lesson can we learn from Marriott’s acquisition of Starwood?
How does the Equifax breach illustrate the importance of Requirement 6.2?
What practical steps can teams take to prevent accidental data exposure like NAB’s?
5.10 Summary; The Price of Complacency
Every breach you’ve just read about could have been prevented by fulfilling one or two existing PCI controls.
That’s what makes these stories haunting.
They prove that compliance is not paperwork, it’s discipline.
It’s patching on time, reviewing logs, verifying vendors, and deleting what you no longer need.
PCI DSS isn’t a shield you buy once; it’s a reflex you practise daily.
“Security fails when familiarity breeds comfort.
Compliance survives when curiosity never sleeps.”



Brillant breakdown of the Target breach lesson. The point about monitoring without response being mere decoration really cuts to the core issue most orgnizations face. FireEye detected the intrusion in real-time but the SOC team's alert fatigue meant nothing happened until it was too late. This maps directly to Requirement 10, but more importantly it highllights how technical controls are meaningless without operational maturity and proper staffing to act on signals.