The secret rulebook behind every tap-and-go payment (Part 5)
From awareness to ownership: the final PCI mindset test
Part 1, Part 2, Part 3, Part 4
Chapter 6: Final Review & Integrative Challenge
By now, you’ve explored the what, why, and how of PCI DSS from understanding its origins and scope, to learning how every architect, developer, tester, and project manager contributes to compliance.
But understanding the standard isn’t the goal.
Applying it instinctively even under pressure, deadlines, and complexity is.
This final chapter helps you bring all the pieces together through real-world scenarios, reflection, and a closing synthesis of the PCI mindset.
6.1 The Real Meaning of “Compliance”
When most people hear the word compliance, they picture checklists and audits. But in PCI, compliance isn’t a destination, it’s a rhythm.
You don’t “get” compliant; you stay compliant, every day, through a thousand small actions.
It’s like driving safely. You don’t pass the driving test once and forget the road rules. Every journey, every traffic light, every weather change demands awareness.
The same applies to PCI.
The audit report or Attestation of Compliance (AoC) is just the snapshot.
The real protection lives in daily behaviour: encrypting data, reviewing logs, patching systems, and keeping curiosity alive.
6.2 The Integrative Scenario; “The New Checkout Project”
Let’s step into a realistic situation that mirrors what many modern teams face.
Your company, AuroraPay, is launching a new checkout microservice to process payments for digital gift cards. You are part of a cross-functional squad with an architect, developers, testers, and a project manager. The CTO has made one thing clear: the system must be PCI DSS compliant by design, no last-minute clean-ups.
You’ve been given this initial plan:
Frontend: A React single-page application (SPA) that collects card details and calls the backend API.
Backend: A Node.js microservice running on AWS Fargate that sends card data to an external payment processor (Adyen).
Database: A PostgreSQL instance storing transactions, order details, and some user metadata.
Logs and Monitoring: CloudWatch for logs, Datadog for metrics.
Project Timeline: 10 weeks until production release.
Everything looks neat. But PCI awareness means seeing what others miss.
Let’s test that awareness.
Challenge Part 1: Scoping the CDE
Question: Which components are in scope for PCI DSS?
At first glance, you might think only the backend API is.
But remember Chapter 2: any system that stores, processes, or transmits cardholder data even temporarily, falls into the Cardholder Data Environment (CDE).
That means:
The React frontend (if it captures raw card numbers)
The API (since it transmits card data)
The network segment where the API runs
The logging and monitoring systems capturing any CHD accidentally
Now imagine the React app is hosted on the same domain as your marketing site. Suddenly, the entire web environment is connected and your PCI scope just exploded.
Challenge Part 2: Designing for Scope Reduction
You propose a different design:
Use Adyen’s hosted payment page or client-side encryption so that the browser never sends raw card data to your backend.
The backend receives only a token, which represents the transaction.
All logs contain order IDs and masked PANs only (e.g. **** **** **** 1234).
The backend stores transaction metadata, but not card numbers.
TLS 1.3 enforced across all communication.
Access to the database restricted by IAM roles and MFA.
Result: The backend is now out of scope for PCI DSS because it never touches CHD or SAD.
Your CDE shrinks to the external payment processor’s domain and the PCI burden moves to them (supported by their AoC).
You’ve achieved the architect’s dream: security through design simplicity.
Challenge Part 3: The Logging Trap
Two sprints later, a developer adds this debug statement:
console.log(”Payment request body:”, JSON.stringify(req.body));
What happens?
That single line, harmless during local testing, writes full card data to CloudWatch logs which sync to Datadog.
In one commit, your observability pipeline becomes part of the CDE.
You’ve turned a one-system scope into a multi-vendor audit nightmare.
Lesson: PCI compliance isn’t about encryption keys or firewalls.
It’s about awareness. Every log, every payload, every variable can either keep you safe or expose your entire environment.
Challenge Part 4: Vendor and People Risks
During testing, the PM signs a contract with an analytics vendor to “track customer purchase behaviour.” The vendor asks for API access to the transaction database.
As an architect, your alarm bells ring:
Analytics systems often aren’t PCI-compliant. If they can access even tokenised data with partial PANs, you may inadvertently expose CHD.
Action Plan:
Verify the vendor’s PCI Attestation of Compliance.
Restrict access via a read-only view with masked data.
Ensure the data export process is logged, encrypted, and approved.
Document this design decision in your PCI scope register.
Meanwhile, a developer leaves the company.
Offboarding fails to revoke their access to CloudWatch. Two weeks later, auditors find an active user account.
PCI DSS violation: Requirement 8, every user must have unique access and timely revocation upon termination.
Small oversights, big consequences.
Challenge Part 5: The Test Data Dilemma
Your QA environment needs sample transactions to verify refunds and partial authorisations.
A new tester, unaware of PCI, exports a few real production transactions “for realism.”
Suddenly, your test environment now holds live card data and therefore, becomes part of the CDE.
Your scope just tripled.
Correct approach:
Use synthetic tokens or dummy card numbers provided by Adyen.
Validate with test-mode APIs only.
Prohibit real data replication across environments.
Automate nightly scans for PAN-like patterns in logs and databases.
Testing securely is as important as coding securely.
6.3 The Human Side of Compliance
PCI DSS is a technical standard, but failures are almost always human.
People skip steps when they’re tired, or they make assumptions when documentation lags.
That’s why Requirement 12, maintaining security policy and training is so essential.
Compliance is sustained not through one-off audits but through habits, rituals, and accountability.
Every person in the PCI ecosystem has a small part to play:
The architect defines safe boundaries.
The developer guards data at the code level.
The tester hunts for leaks before they spread.
The project manager ensures processes don’t drift.
Individually, each role might seem minor. Together, they build resilience.
“PCI isn’t a firewall. It’s a culture of carefulness.”
6.4 Reflection Exercise; The Team Retrospective
Imagine your squad has just completed the AuroraPay project.
During your sprint retrospective, your manager asks three questions:
What did we do well in our PCI implementation?
Where did we take unnecessary risks or shortcuts?
How can we make compliance automatic next time?
Spend a few minutes writing honest answers from your perspective and from another role’s.
For instance:
If you’re a developer, how can you make life easier for testers?
If you’re a PM, how can you ensure architects have enough time for design reviews?
If you’re a tester, how can you share findings that influence coding standards?
Compliance is teamwork under pressure. Reflection keeps the team humble and sharp.
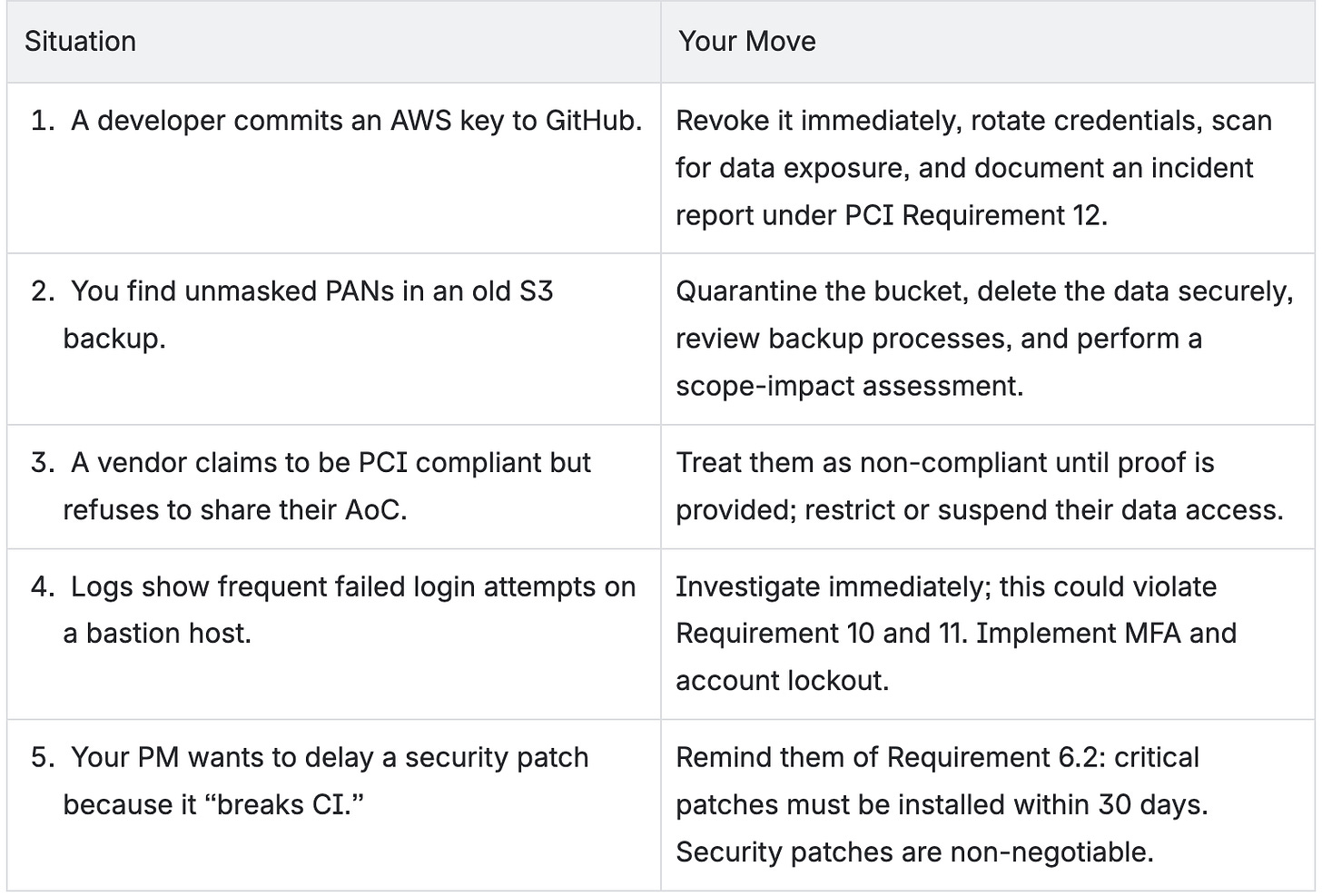
6.5 The “What If?” Game
Let’s test your instincts with short, thought-based scenarios.
These “micro-decisions” are where PCI lives or dies.
Every choice above affects multiple requirements — from access control to vulnerability management.
6.6 Group Discussion Prompts
Use these prompts for a 20-minute discussion:
How can your organisation make PCI training less of a compliance exercise and more of a shared culture?
Which PCI controls feel most natural to your role? Which feel alien?
What would a “PCI by Design” culture look like in your product teams?
Should PCI be integrated into sprint reviews, definition of done, or architecture sign-off?
How can you collaborate with vendors to share responsibility transparently?
The goal isn’t to find right answers, it’s to surface blind spots.
6.7 The Final Checklist; Can You Explain PCI in Plain English?
By the end of this course, you should be able to explain PCI DSS without jargon.
Try this exercise:
“Explain PCI DSS to a new engineer in two minutes.”
Here’s a model answer:
“PCI DSS is a global security standard that protects payment card data.
It applies to anyone who stores, processes, or transmits cardholder data.
The goal is to minimise where that data exists and secure it through encryption, restricted access, and continuous monitoring.
It has 12 core requirements — things like firewalls, secure coding, and logging.
Compliance isn’t just about passing audits; it’s about building systems that keep customer trust safe every day.”
If you can deliver that confidently, you’ve achieved awareness, the purpose of this entire program.
6.8 From Awareness to Ownership
Take ten minutes and write a brief “PCI Pledge” in your own words.
What habits will you personally maintain after this course?
Here are a few examples:
I will never store or log unmasked card data, even temporarily.
I will challenge designs that blur PCI boundaries, no matter who proposes them.
I will keep learning about new attack patterns and mitigation techniques.
I will treat compliance as part of engineering excellence, not bureaucracy.
Awareness without ownership fades. Ownership turns rules into reflex.
6.9 Building a PCI Mindset
Let’s close the loop.
PCI DSS isn’t about avoiding fines or impressing auditors. It’s about protecting trust the invisible currency behind every tap, click, and swipe.
When you secure cardholder data, you protect not only your customers but also your team’s integrity and your company’s reputation.
Across these six chapters, you’ve learned to:
Understand why PCI DSS exists and what it protects.
Identify what data is in scope and how to reduce exposure.
Apply the 12 requirements in plain, practical language.
See how each role contributes to compliance daily.
Learn from real-world breaches where negligence had a cost.
Integrate all of this into one coherent mindset: design small, protect deeply, monitor continuously.
If you take nothing else away, remember this truth:
PCI DSS is not a standard for computers, it’s a standard for people who build them responsibly.
6.10 Mini-Final Quiz
What is the fastest way to reduce PCI scope in an application design?
Why must test environments follow the same rules as production?
Which three requirements would be violated by logging raw PANs?
What human behaviour caused most major PCI breaches discussed in Chapter 5?
What’s the difference between compliance and security in practice?
What one action can you personally take tomorrow to strengthen PCI compliance at work?
The Quiet Confidence
True PCI mastery isn’t loud. It doesn’t rely on security slogans or compliance badges.
It’s quiet, the calm confidence that every line of code, every diagram, every decision was made with respect for the people whose data you hold.
You’ll never meet most of them. They’ll never know your name. But their trust is in your hands every time they swipe or click.
And that is what being PCI-aware truly means.